Configuring Azure Active Directory
The images below may vary in practice.
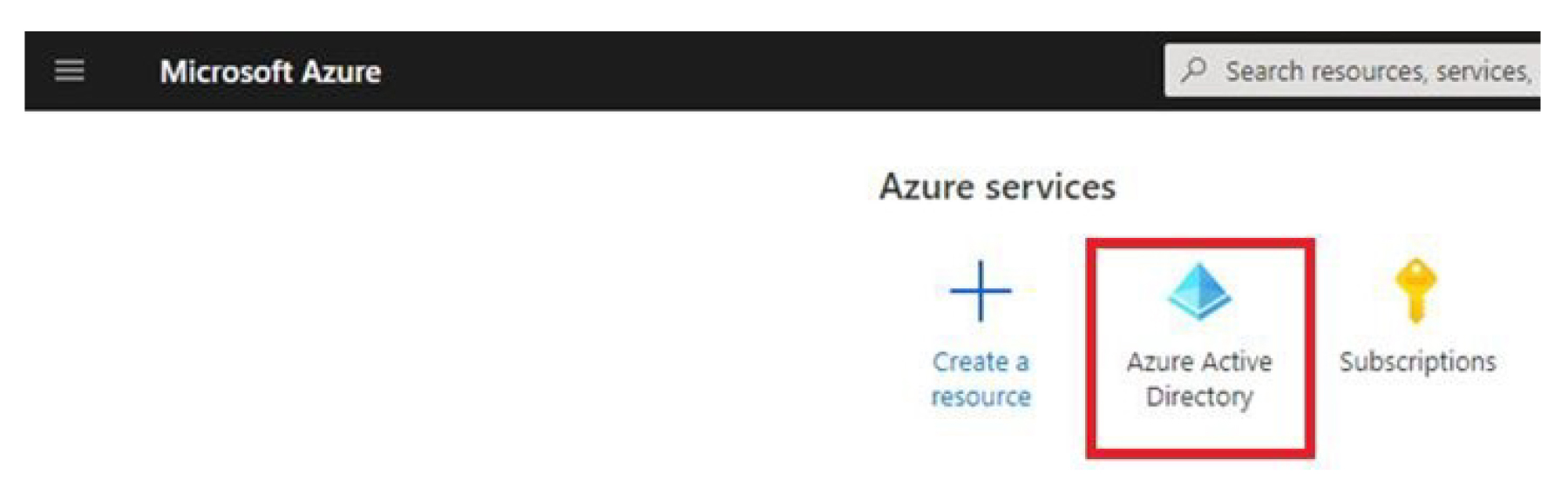
From the Azure portal, navigate to the Azure Active Directory.
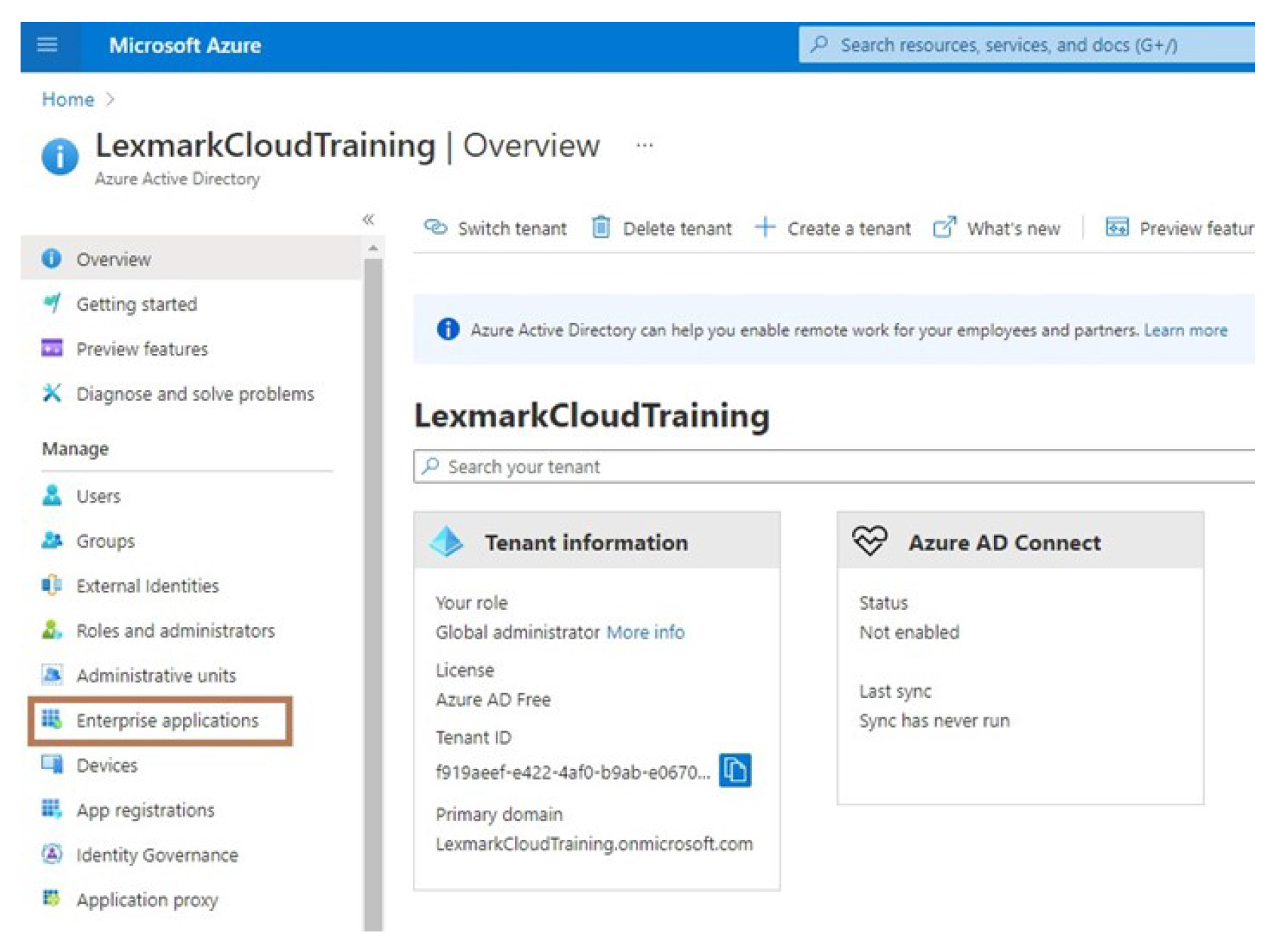
Click Enterprise applications > New application.

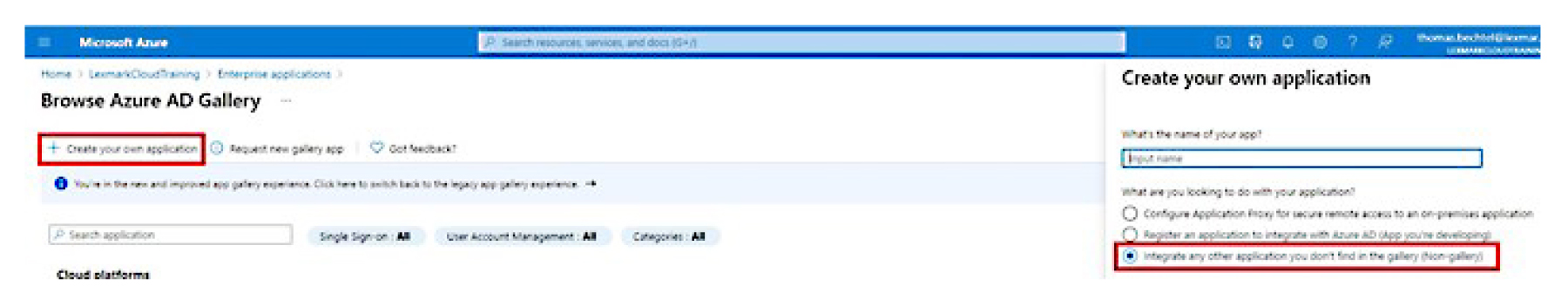
Click Create your own application > Integrate any other application you don’t find in the gallery (Non-gallery).
Type an application name.
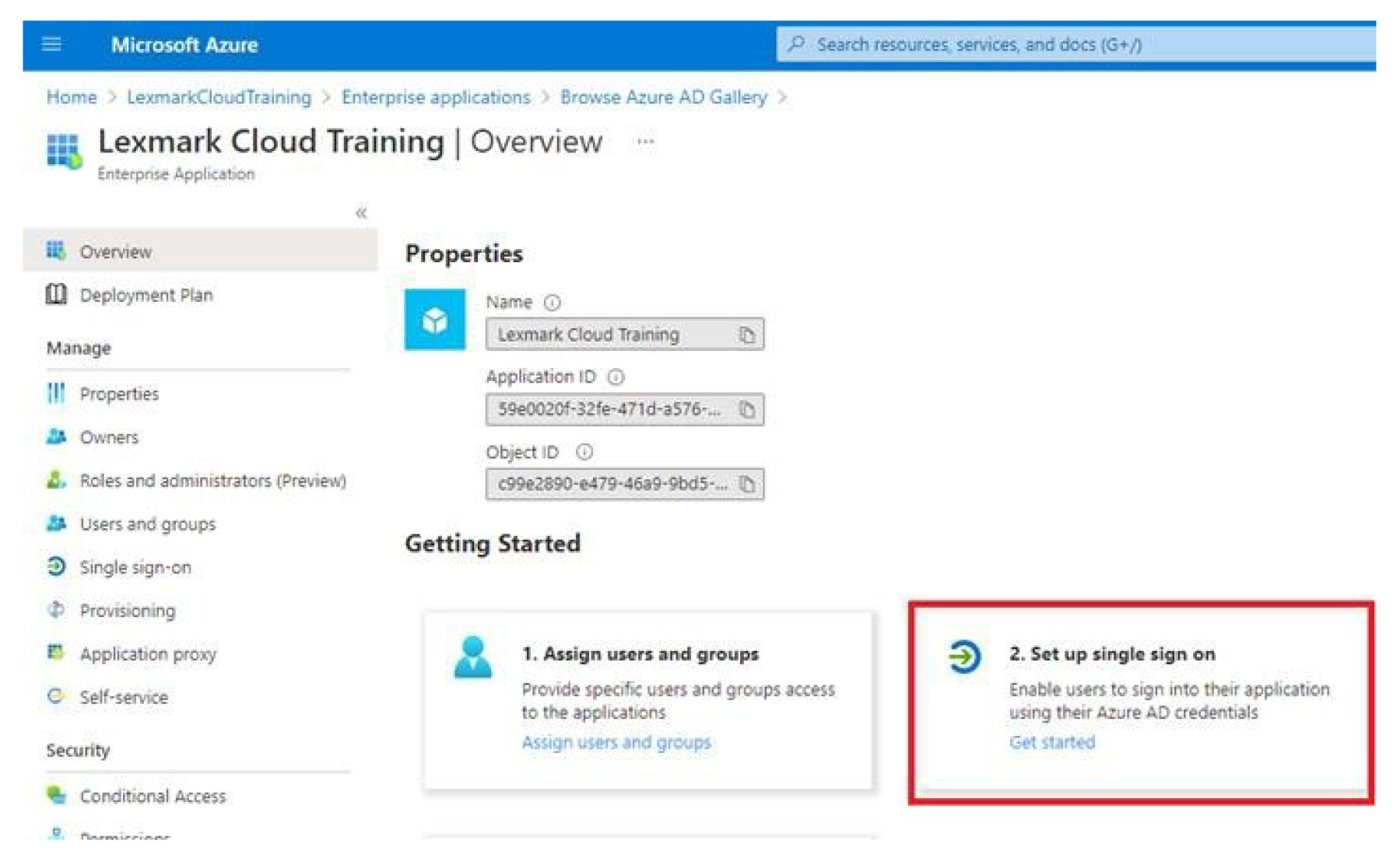
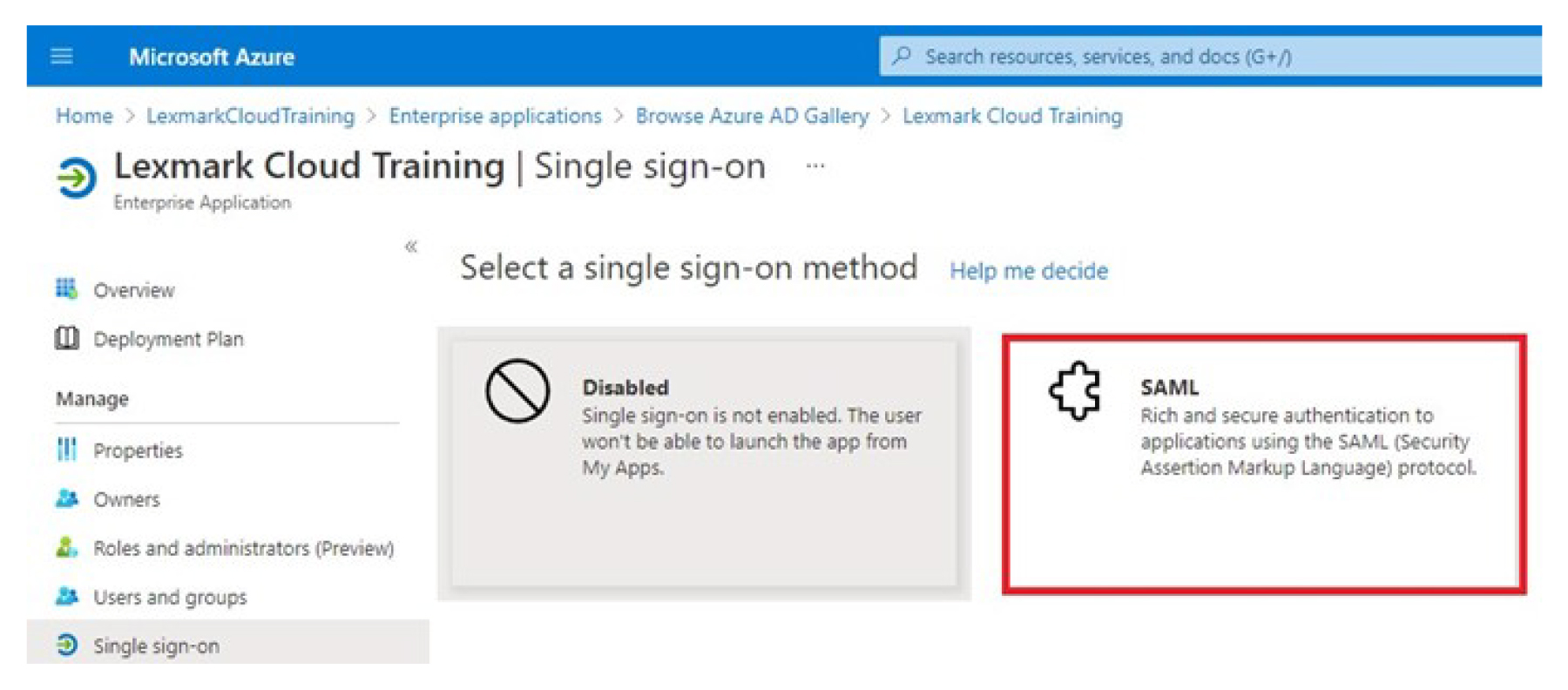
From the Enterprise Applications Overview screen, click Set up single sign on, and then select SAML.
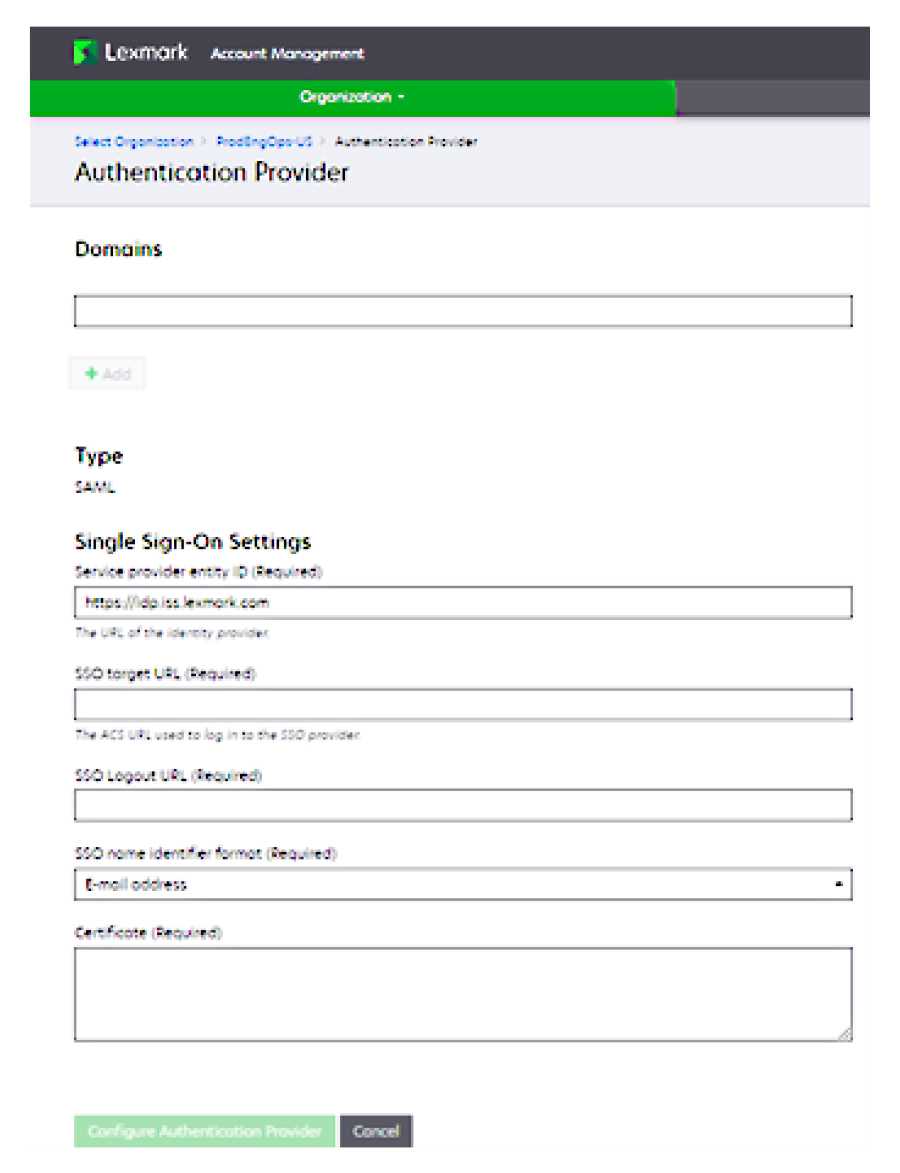
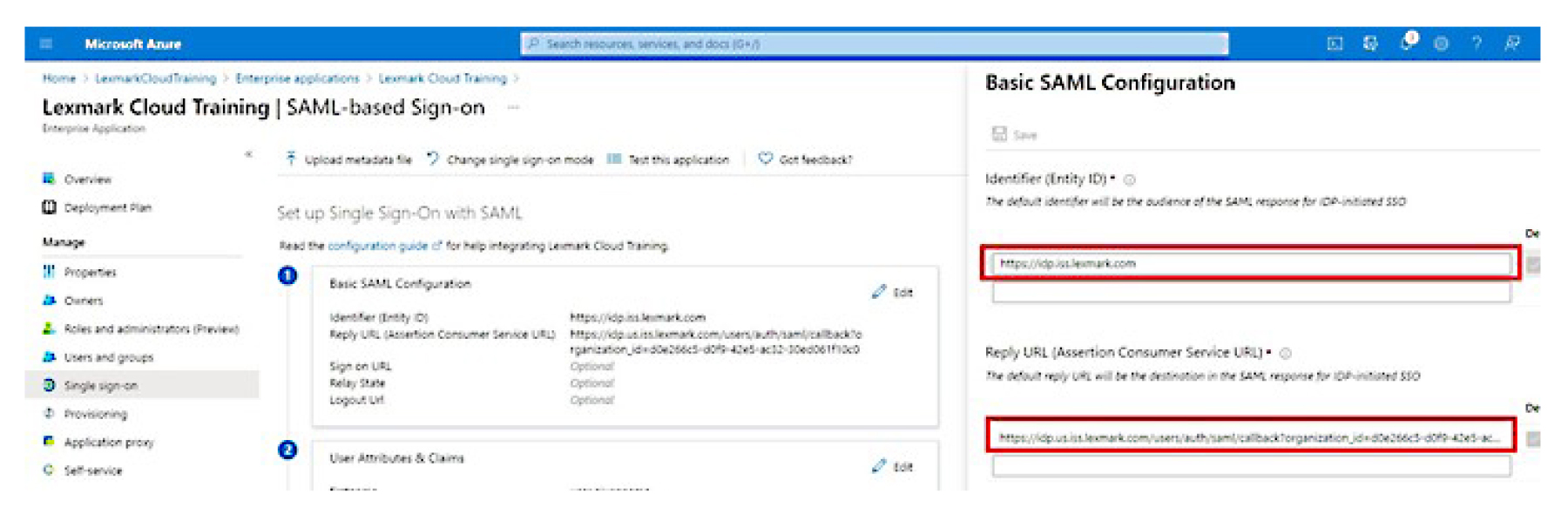
From the Basic SAML Configuration section, configure the following settings:
 Note: Obtain the settings from the service provider.
Note: Obtain the settings from the service provider.Identifier (Entity ID)
Note: The default Lexmark Cloud Services entity ID is https://idp.iss.lexmark.com. Make sure that the entity ID in Azure matches the entity ID in the Lexmark Cloud Services portal.Reply URL (Assertion Consumer Service URL)
Depending on your location, the following are examples of a full reply URL:
https://idp.us.iss.lexmark.com/users/auth/saml/callback?organization_id=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXXX
https://idp.eu.iss.lexmark.com/users/auth/saml/callback?organization_id=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXXX
Note: To determine the value for the organization_id parameter, log in to the Lexmark Cloud Services portal, and then click Account Management. The organization_id appears in the URL.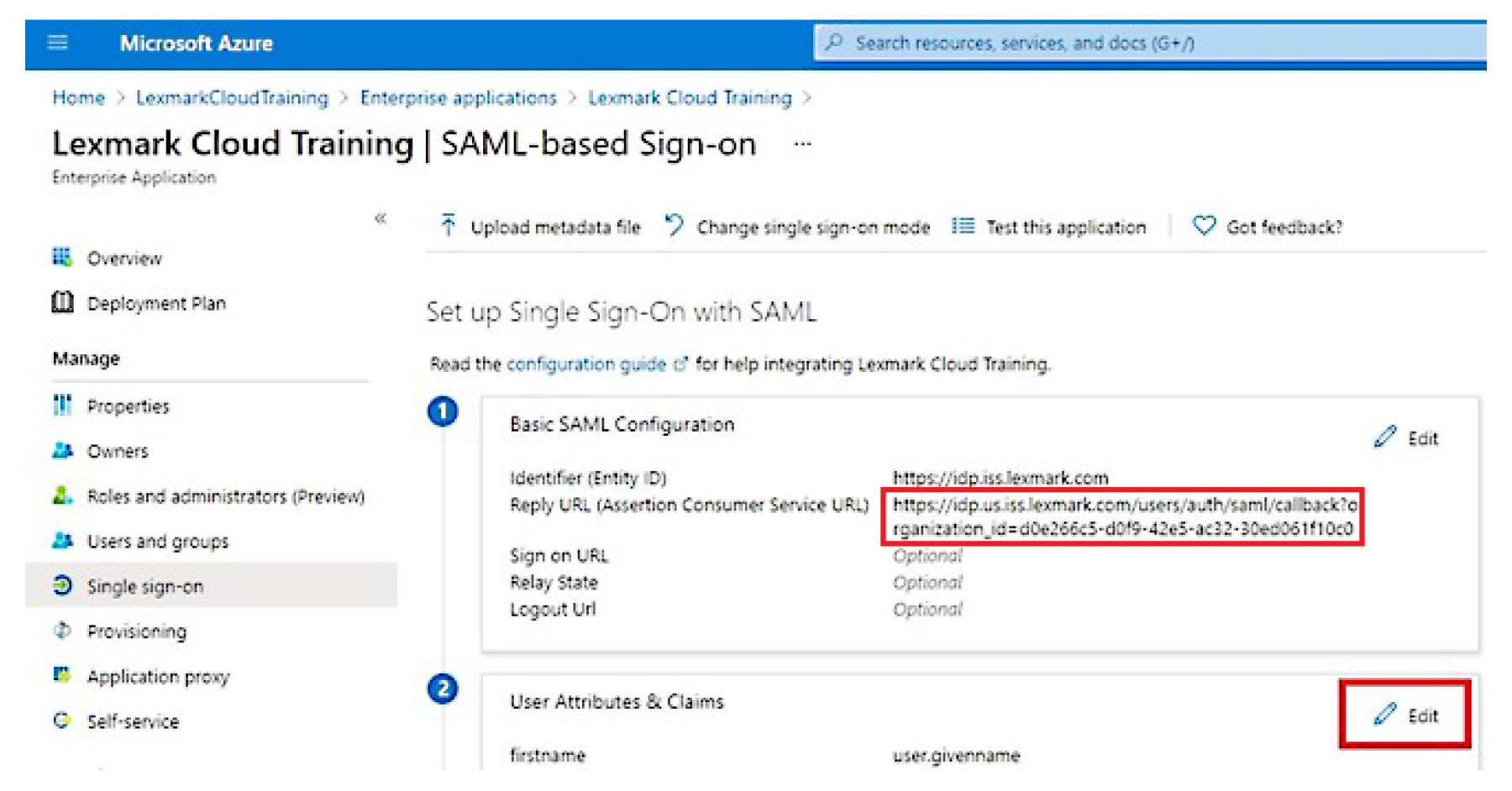
From the User Attributes & Claims section, click Edit.
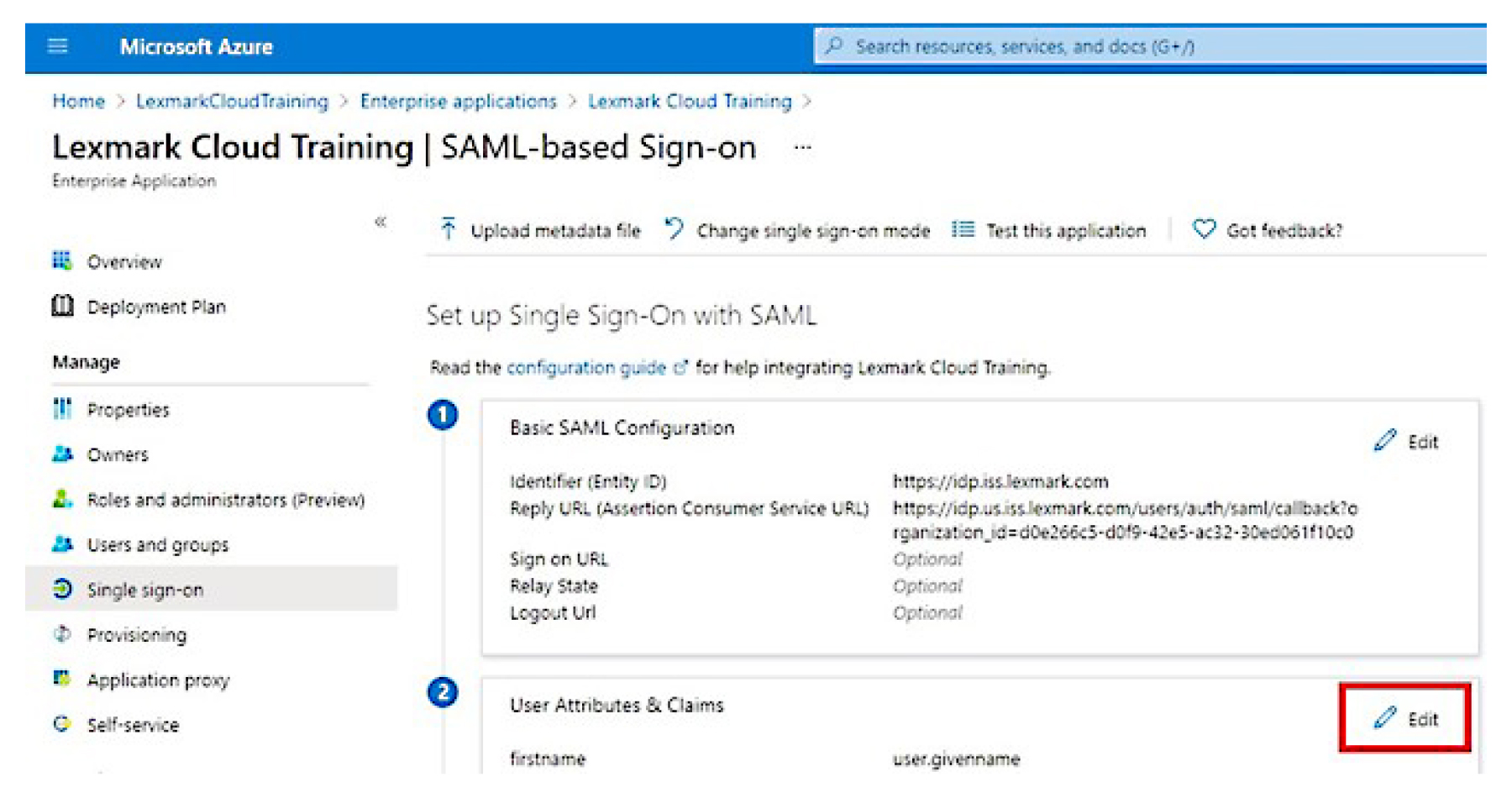
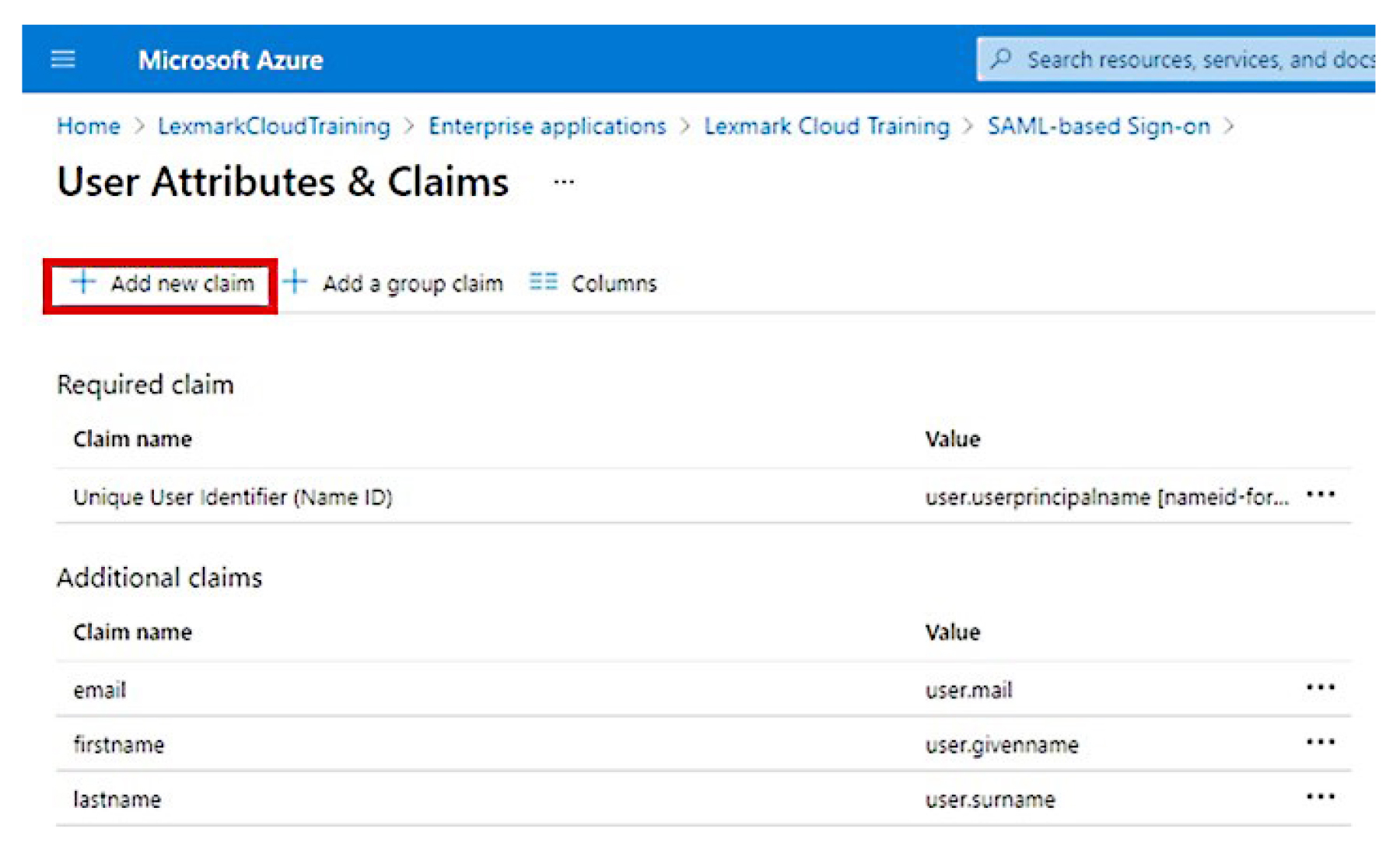
Click Add new claim, and then type the name and source for each claim.
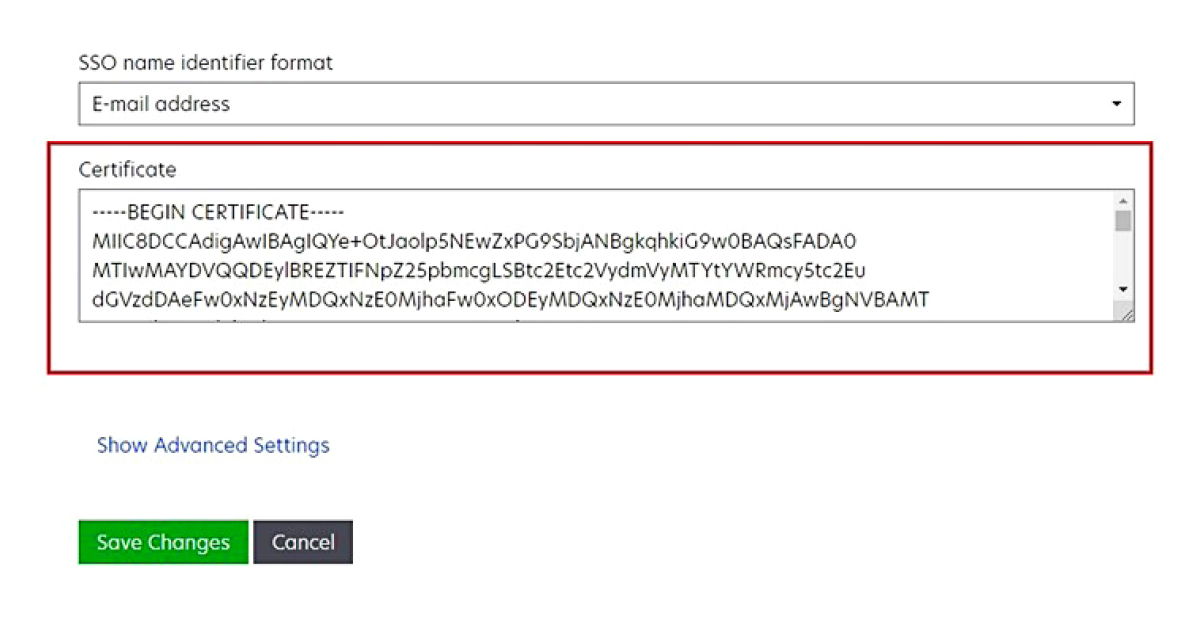
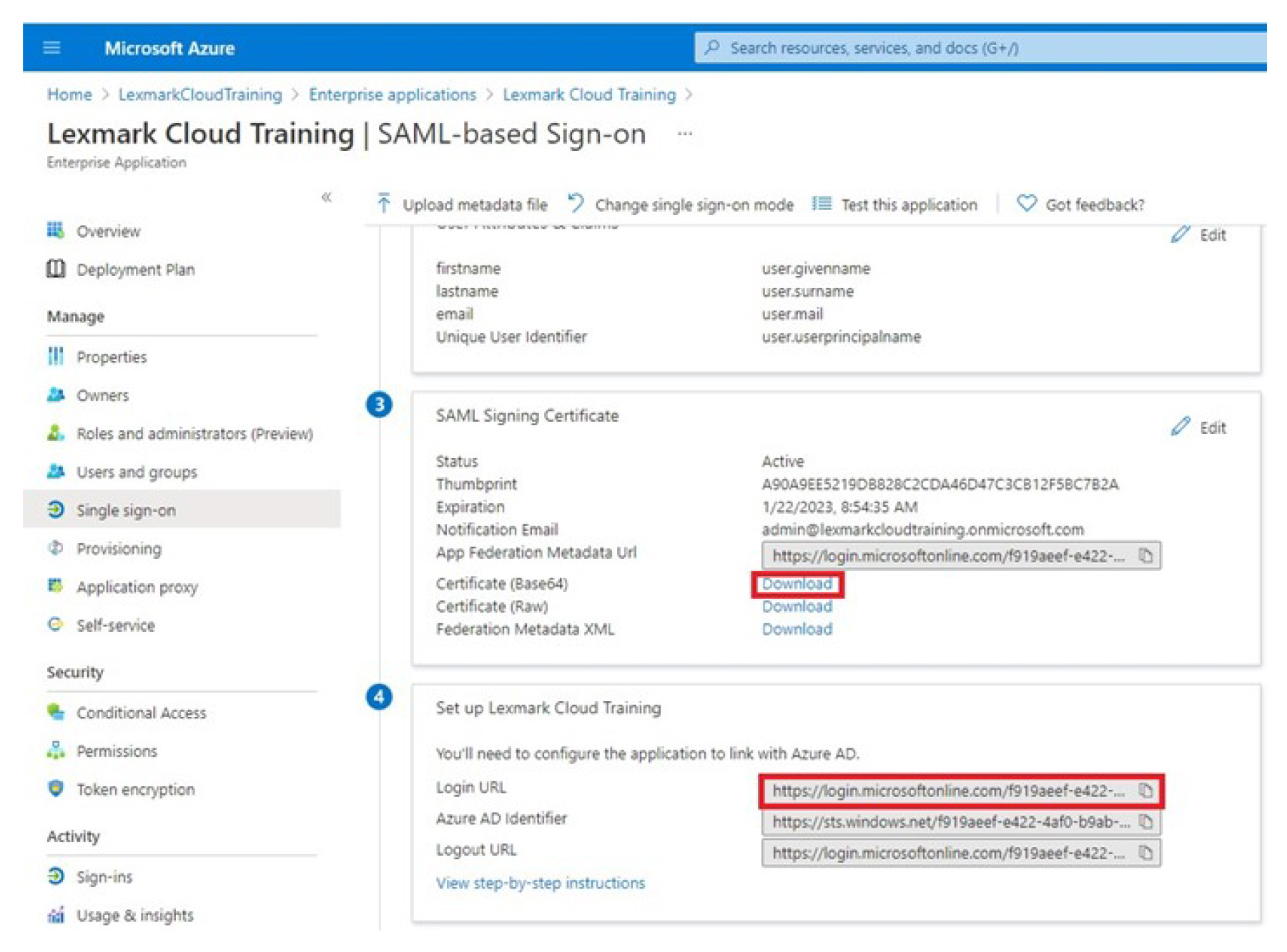
From the SAML Signing Certificate section, do the following:
Download the Base64 certificate.
Copy the login and logout URLs.
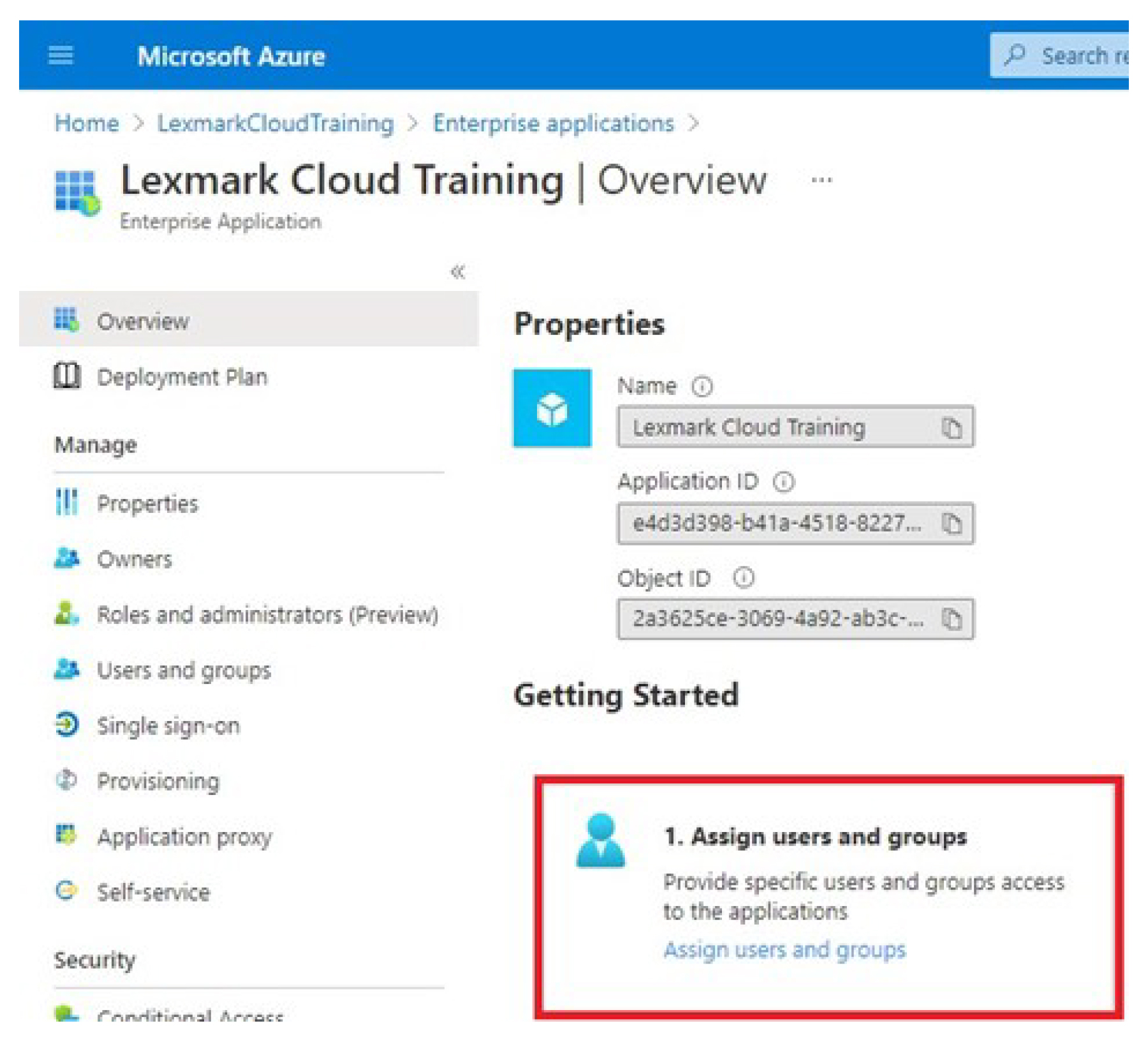
Depending on your Azure configuration, assign users to the created enterprise application.
Save the settings.