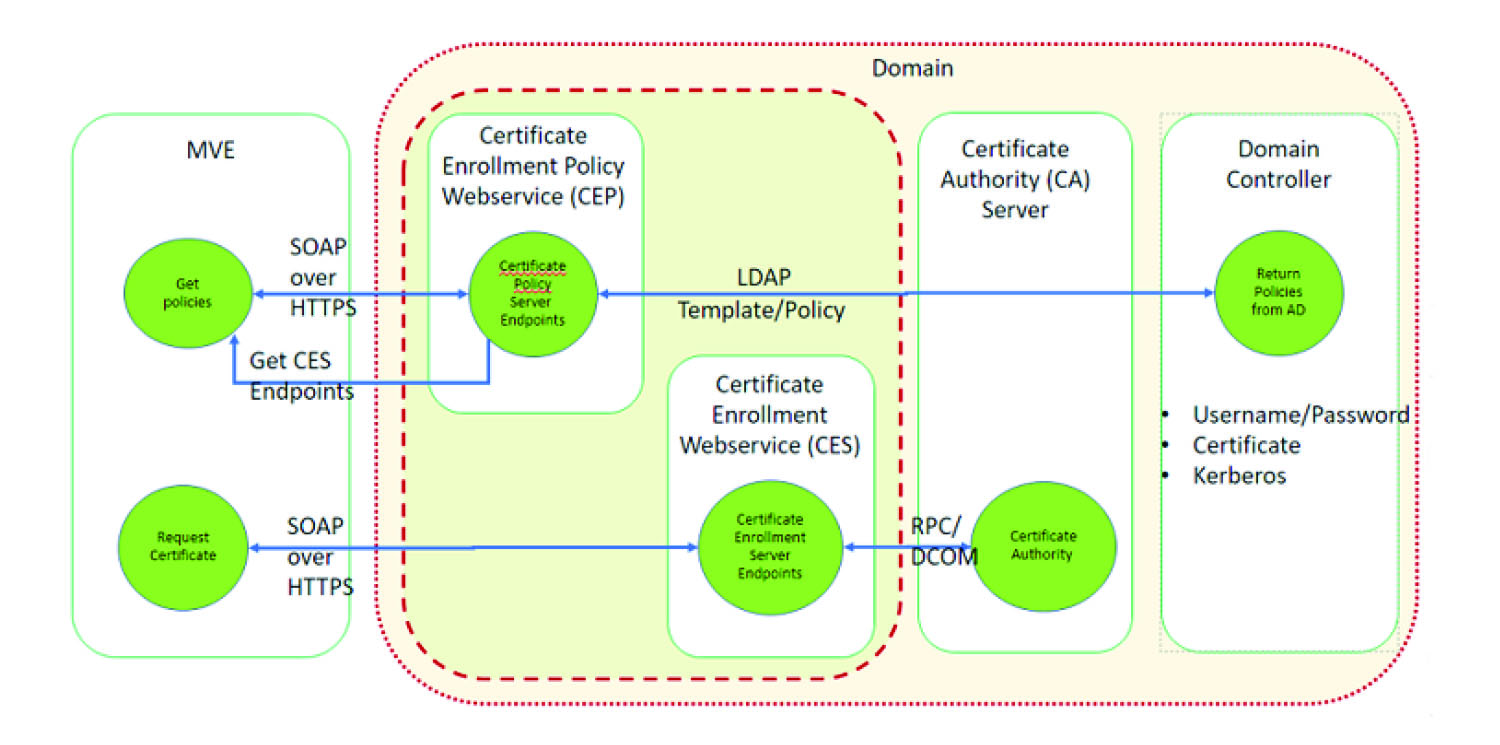
Managing certificates using Microsoft Certificate Authority through MSCEWS
This section provides information on configuring Certificate Enrollment Policy Web Service (CEP) and Certificate Enrollment Web Service (CES). As Microsoft recommends installing CEP and CES in two different machines, we are following the same in this document. We refer to these web services as CEP server and CES server, respectively.
Note: The user must have a preconfigured Enterprise Certificate Authority (CA) and a domain controller.
System requirements
The Windows Server 2012 R2 and onwards operating system is used for all setups in this section. The following installation requirements and capabilities apply to both CEP and CES, unless otherwise specified.
Create the following types of accounts in the domain controller:
Network connectivity requirements
Network connectivity requirements are a key part of deployment planning, particularly for scenarios where the CEP and CES are hosted in a perimeter network.
All client connectivity to both services occurs within an HTTPS session, so only HTTPS traffic is allowed between the client and the web services.
CEP communicates with Active Directory Domain Services (AD DS), using standard Lightweight Directory Access Protocol (LDAP) and secure LDAP (LDAPS) ports (TCP 389 and 636 respectively).
CES communicates with CA using Distributed Component Object Model (DCOM).
Notes:
- By default, DCOM uses random ephemeral ports.
- CA can be configured to reserve a specific range of ports to simplify firewall configuration.
Creating SSL certificates for CEP and CES servers
CES and CEP must use Secure Sockets Layer (SSL) for communication with clients (by using HTTPS). Each service must have a valid certificate that has an Enhanced Key Usage (EKU) policy of server authentication in the local computer certificate store.
Install the IIS service in the server.
Log in to the CEP server, and then add the Root CA certificate in the Trusted Root Certification Authority store.
Launch the IIS Manager Console and then, select Server Home.
From the main view section, open Server Certificates.
Click Actions > Create Certificate Request.
In the Distinguished Name Properties window, provide the necessary information and then, click Next.
In the Cryptographic Service Provider Properties dialog, select the bit length, and then click Next.
Save the file.
Get the file signed by the CA that you are planning to use for CEP and CES.
Note: Make sure that Server Authentication EKU is enabled in the signed certificate.
Copy the signed file back to the CEP server.
From the IIS Manager Console, select Server Home.
From the Main View section, open Server Certificates.
Click Actions > Complete Certificate Request.
In Specify Certificate Authority Response window, select the signed file.
Type a name, and then in the Certificate Store menu, select Personal.
Complete the certificate installation.
From IIS Manager Console, select the default website.
Click Actions > Bindings.
In the Site Bindings dialog, click Add.
In the Add Site Binding dialog, set Type to https, and then from the SSL certificate, browse for the newly created certificate.
From the IIS Manager Console, select Default Web Site, and then open the SSL settings.
Enable Require SSL and set Client certificates to Ignore.
Restart IIS.
Note: Follow the same process for CES server.
Creating certificate templates
The user must create a certificate template for the certificate enrollment. Do the following to copy from an existing certificate template:
Log in to the Enterprise CA with CA administrator credentials.
Expand the CA, right-click Certificate Templates, and then click Manage.
In the Certificate Templates Console, right-click Web Server Certificate Template, and then click Duplicate Template.
From the General tab of the template, name the template MVEWebServer.
In the Security tab, give the CA administrator Read, Write, and Enroll permissions.
Give Read and Enroll permissions to the authenticated users.
In the Subject Name tab, select Supply in the request.
In the General tab, set the certificate validity period.
If you plan to use this certificate template for issuing a 802.1X Certificate for printers, then do the following:
From the Extensions tab, select Application Policies from the list of extensions included in this template.
Click Edit > Add.
In Add Application Policy dialog box, select Client Authentication.
Click OK.
In the Certificate Template Properties dialog box, click OK.
In the CA window, right-click Certificate Templates, and then click New > Certificate template.
Select MVEWebServer, and then click OK.
Understanding authentication methods
CEP and the CES support the following authentication methods:
Windows-integrated authentication, also known as Kerberos Authentication
Client certificate authentication, also known as X.509 Certificate Authentication
Username and Password Authentication
Windows-integrated authentication
Windows-integrated authentication uses Kerberos to provide an uninterrupted authentication flow for devices connected to the internal network. This method is preferred for internal deployments because it uses the existing Kerberos infrastructure within AD DS. It also requires minimal changes to certificate client computers.
Note: Use this authentication method if you need clients to access only the web service while connected directly to your internal network.
Client certificate authentication
This method is preferred over user name and password authentication because it is more secure. It does not require a direct connection to the corporate network.
Notes:
- Use this authentication method if you plan to provide clients with digital X.509 certificates for authentication.
- This method enables the web services available on the Internet.
User name and password authentication
The user name and password method is the simplest form of authentication. This method is typically used for servicing clients who are not directly connected to the internal network. It is a less secure authentication option than client certificate authentication, but it does not require provisioning a certificate.
Note: Use this authentication method when you can access the web service on the internal network or over the Internet.
Delegation requirements
Delegation enables a service to impersonate a user or computer account to access resources throughout the network.
Delegation is required for the CES server when all the following scenarios apply:
CA and CES are not residing on the same computer.
CES can process initial enrollment requests, as opposed to only processing certificate renewal requests.
The authentication type is set to Windows-integrated authentication or Client certificate authentication.
Delegation is not required for the CES server in the following scenarios:
Notes:
- Microsoft recommends running CEP and CES as domain user accounts.
- Users must create an appropriate service principal name (SPN) before configuring delegation on the domain user account.
Enabling delegation
To create an SPN for a domain user account, use the setspn command as follows:
setspn -s http/ces.msca.com msca\CESSvc
Notes:
- The account name is CESSvc.
- CES is running on a computer with a fully qualified domain name (FQDN) of ces.msca.com in the msca.com domain.
After running the setspn command, open the CESSvc domain user account in the domain controller.
From the Delegation tab, select Trust this user for delegation to specified services only.
Select the appropriate delegation based on the authentication method.
Notes:
- If you select Windows-integrated authentication, then configure delegation to use Kerberos only.
- If the service is using client certificate authentication, then configure delegation to use any authentication protocol.
- If you plan to configure multiple authentication methods, then configure delegation to use any authentication protocol.
Click Add.
In the Add Services dialog box, select Users or Computers.
Type your CA server host name, and then click Check Names.
From the Add Services dialog box, select either of the following services to delegate:
Close the domain user properties dialog box.
Configuring windows-integrated authentication
To install CEP and CES, use Windows PowerShell.
Configuring CEP
The Install-AdcsEnrollmentPolicyWebService cmdlet configures the Certificate Enrollment Policy Web Service (CEP). It is also used to create other instances of the service within an existing installation.
Log in to the CEP server using CEPAdmin user name, and then launch PowerShell in administrative mode.
Run the command Import-Module ServerManager.
Run the command Add-WindowsFeature Adcs-Enroll-Web-Pol.
Run the command Install-AdcsEnrollmentPolicyWebService -AuthenticationType Kerberos -SSLCertThumbprint "sslCertThumbPrint".
Note: Replace <sslCertThumbPrint> with the thumbprint of the SSL certificate created for the CEP server, after deleting the spaces between the thumbprint values.
Complete the installation either by selecting either Y or A.
Launch the IIS Manager Console.
In the Connections pane, expand the web server that is hosting CEP.
Expand Sites, expand Default Web Site, and then click the appropriate installation virtual application name, ADPolicyProvider_CEP_Kerberos.
In the virtual application called Home , double-click the application settings, and then double-click FriendlyName.
Type a name under Value, and then close the dialog.
Double-click URI, and then copy Value.
Notes:
- If you want to configure another authentication method on the same CEP server, then you must change the ID.
- This URL is used in MVE or any client application.
From the left pane, click Application Pools.
Select WSEnrollmentPolicyServer, and then from the right pane, click Actions > Advanced Settings .
Select the identity field under Process Model.
In the Application Pool Identity dialog box, select the custom account, and then type CEPSvc as the domain user name.
Close all dialog boxes, and then recycle IIS from the right pane of the IIS Manager Console.
From PowerShell, type iisreset to restart IIS.
Configuring CES
The Install-AdcsEnrollmentWebService cmdlet configures the Certificate Enrollment Web Service (CES). It is also used to create other instances of the service within an existing installation.
Log in to the CES server using CESAdmin user name and launch PowerShell in administrative mode.
Run the command Import-Module ServerManager.
Run the command Add-WindowsFeature Adcs-Enroll-Web-Svc.
Run the command Install-AdcsEnrollmentWebService -ApplicationPoolIdentity -CAConfig "CA1.contoso.com\contoso-CA1-CA" -SSLCertThumbprint "sslCertThumbPrint" -AuthenticationType Kerberos.
Notes:
- Replace <sslCertThumbPrint> with the thumbprint of the SSL certificate created for the CES server, after deleting the spaces between the thumbprint values.
- Replace CA1.contoso.com with your CA computer name.
- Replace contoso-CA1-CA with your CA common name.
Complete the installation by selecting either Y or A.
Launch the IIS Manager Console.
In the Connections pane, expand the web server that is hosting CES.
Expand Sites, expand Default Web Site, and then click the appropriate installation virtual application name: contoso-CA1-CA _CES_Kerberos.
From the left pane, click Application Pools.
Select WSEnrollmentPolicyServer, and then from the right pane, click Actions > Advanced Settings .
Select the identity field under Process Model.
In the Application Pool Identity dialog box, select the custom account, and then type CESSvc as the domain user name.
Close all dialog boxes, and then recycle IIS from the right pane of IIS Manager Console.
From PowerShell, type iisreset to restart IIS.
For CESSvc domain user, enable delegation. For more information, see Enabling delegation.
Configuring client certificate authentication
Configuring CEP
The Install-AdcsEnrollmentPolicyWebService cmdlet configures CEP. It is also used to create other instances of the service within an existing installation.
Log in to the CEP server using CEPAdmin user name, and then launch PowerShell in administrative mode.
Run the command Import-Module ServerManager.
Run the command Add-WindowsFeature Adcs-Enroll-Web-Pol.
Run the command Install-AdcsEnrollmentPolicyWebService -AuthenticationType Certificate -SSLCertThumbprint “sslCertThumbPrint”.
Note: Replace <sslCertThumbPrint> with the thumbprint of the SSL certificate created for the CEP server, after deleting the spaces between the thumbprint values.
Complete the installation by selecting either Y or A.
Launch the IIS Manager Console.
In the Connections pane, expand the web server that is hosting CEP.
Expand Sites, expand Default Web Site, and then click the appropriate installation virtual application name ADPolicyProvider_CEP_Certificate.
In the virtual application called Home , double-click the application settings, and then double-click FriendlyName.
Type a name under Value and close the dialog.
Double-click URI, and then copy Value.
Notes:
- If you want to configure another authentication method on the same CEP server, then you must change the ID.
- This URL is used in MVE or any client application.
From the left pane, click Application Pools.
Select WSEnrollmentPolicyServer, and then from the right pane, click Actions > Advanced Settings.
Select the identity field under Process Model.
In the Application Pool Identity dialog box, select the custom account, and then type CEPSvc as the domain user name.
Close all dialog boxes, and then recycle IIS from the right pane of the IIS Manager Console.
From PowerShell, type iisreset to restart IIS.
Configuring CES
The Install-AdcsEnrollmentWebService cmdlet configures the Certificate Enrollment Web Service (CES). It is also used to create other instances of the service within an existing installation.
Log in to the CES server using CESAdmin user name, and then launch PowerShell in administrative mode.
Run the command Import-Module ServerManager.
Run the command Add-WindowsFeature Adcs-Enroll-Web-Svc.
Run the command Install-AdcsEnrollmentWebService -ApplicationPoolIdentity -CAConfig “CA1.contoso.com\contoso-CA1-CA” -SSLCertThumbprint “sslCertThumbPrint” -AuthenticationType Certificate.
Notes:
- Replace <sslCertThumbPrint> with the thumbprint of the SSL certificate created for the CES server, after deleting the spaces between the thumbprint values.
- Replace CA1.contoso.com with your CA computer name.
- Replace contoso-CA1-CA with your CA common name.
- If you have already configured one authentication method in the host, then remove ApplicationPoolIdentity from the command.
Complete the installation either by selecting Y or A.
Launch the IIS Manager Console.
In the Connections pane, expand the web server that is hosting CEP.
Expand Sites, expand Default Web Site, and then click the appropriate installation virtual application name: contoso-CA1-CA _CES_Certificate.
From the left pane, click the Application Pools.
Select WSEnrollmentPolicyServer, and then from the right pane, click Actions > Advanced Settings.
Select the identity field under Process Model.
In Application Pool Identity dialog box, select the custom account, and then type CESSvc as the domain user name.
Close all dialog boxes, and then recycle IIS from the right pane of the IIS Manager Console.
From PowerShell, type iisreset to restart IIS.
For CESSvc domain user, enable delegation. For more information, see Enabling delegation.
Configuring username-password authentication
Configuring CEP
The Install-AdcsEnrollmentPolicyWebService cmdlet configures the Certificate Enrollment Policy Web Service (CEP). It is also used to create other instances of the service within an existing installation.
Log in to the CEP server using CEPAdmin user name, and then launch PowerShell in administrative mode.
Run the command Import-Module ServerManager.
Run the command Add-WindowsFeature Adcs-Enroll-Web-Pol.
Run the command Install-AdcsEnrollmentPolicyWebService -AuthenticationType UserName -SSLCertThumbprint “sslCertThumbPrint”.
Note: Replace <sslCertThumbPrint> with the thumbprint of the SSL certificate created for the CEP server, after deleting the spaces between the thumbprint values.
Complete the installation by selecting either Y or A.
Launch the IIS Manager Console.
In the Connections pane, expand the web server that is hosting CEP.
Expand Sites, expand Default Web Site, and then click the appropriate installation virtual application name: ADPolicyProvider_CEP_UsernamePassword.
In the virtual application called Home , double-click the application settings, and then double click FriendlyName.
Type a name under Value and close the dialog.
Double-click URI, and then copy Value.
Notes:
- If you want to configure another authentication method on the same CEP server, then you must change the ID.
- This URL is used in MVE or any client application.
From the left pane, click Application Pools.
Select WSEnrollmentPolicyServer, and then from the right pane, click Actions > Advanced Settings.
Select the identity field under Process Model.
In the Application Pool Identity dialog box, select the custom account, and then type CEPSvc.
Close all dialog boxes, and then recycle IIS from the right pane of the IIS Manager Console.
From PowerShell, type iisreset to restart IIS.
Configuring CES
The Install-AdcsEnrollmentWebService cmdlet configures the Certificate Enrollment Web Service (CES). It is also used to create other instances of the service within an existing installation.
Log in to the CES server using CESAdmin user name, and then launch PowerShell in administrative mode.
Run the command Import-Module ServerManager.
Run the command Add-WindowsFeature Adcs-Enroll-Web-Svc.
Run the command Install-AdcsEnrollmentWebService -ApplicationPoolIdentity -CAConfig “CA1.contoso.com\contoso-CA1-CA” -SSLCertThumbprint “sslCertThumbPrint” -AuthenticationType UserName.
Notes:
- Replace <sslCertThumbprint> with the thumbprint of the SSL certificate created for the CES server, after deleting the spaces between the thumbprint values.
- Replace CA1.contoso.com with your CA computer name.
- Replace contoso-CA1-CA with your CA common name.
- If you have already configured one authentication method in the host, then remove ApplicationPoolIdentity from the command.
Complete the installation by selecting either Y or A.
Launch the IIS Manager Console.
In the Connections pane, expand the web server that is hosting CES.
Expand Sites, expand Default Web Site, and then click the appropriate installation virtual application name: contoso-CA1-CA_CES_UsernamePassword.
From the left pane, click Application Pools.
Select WSEnrollmentPolicyServer, and then from the right pane, click Actions > Advanced Settings under Actions.
Select the identity field under Process Model.
In the Application Pool Identity dialog box, select the custom account, and then type CESSvc as the domain user name.
Close all dialog boxes, and then recycle IIS from the right pane of IIS Manager Console.
From PowerShell, type iisreset to restart IIS.
Configuring MVE
Before configuring the automated certificate management endpoint in MVE, you must make some additional changes in the platform.properties configuration file.
The location of this file is <MVE install dir>/Lexmark/Markvision Enterprise/apps/dm-mve/WEB-INF/classes.
Perform the following steps:
Open the platform.properties file in Notepad++ or a similar text editor in administrator mode.
Find the mscews.ces.hostname key, and then change its value with the host name of your CES server.
Note: The default value is cesserver.
Find the mscews.cep.templateName key, and then change its value with the name of the template that you have created.
Note: The default value of this field is CEPWebServer.
Save the file, and then restart the MVE service.
Log in to MVE, go to the Certificate Authority page, and then follow the instructions to configure the service.
Notes:
- If you are planning to use client certificate authentication method, then you must obtain the valid client certificate from CA.
- In the certificate client certificate authentication, make sure that EKU is enabled.